The latest version of Magento 2.3.5. has new security functionality introduced: The Content Security Policy (CSP). This new functionality is a great addition to the security options Magento already offers, and is considered a best practice for securing your shop. But what is a CSP and why should you apply it?
What is Content Security Policy (CSP)
A website contains (many) different scripts. These scripts provide extra functionalities in your webshop, make sure the customer journey on the website is measured or keep track of how many of your ads convert. Measuring your website via Google Analytics, for example, is done via a script that is loaded.
Most scripts are used for good purposes. Unfortunately, there are also scripts that you should keep out of your webshop. An example is a script that transmits credit card data and passwords to hackers. These scripts can only be placed when a hacker has gained access to the webshop via leaked admin data or via a exploit in an extension, the template or a bug in Magento itself.
Of course, the chances of this happening are minimal if you keep your webshop and extensions well up-to-date. However, there are past examples of attacks that have been successful. The most well-known attack is that of the Magecart group that managed to channel personal data on a large scale through scripts.
This is where a CSP comes in handy. A CSP is a rule on the website that instructs the browser which scripts can be loaded. Scripts that are not included in the CSP will also not be loaded by the browser. The CSP is a Last line of defence because the script is already placed on the website but simply cannot be activated by the visitor. This prevents data from being falsely siphoned off from your website. Besides stopping scripts that are not allowed, a CSP also sends a notification when a script is not included in the CSP. This can then be acted upon quickly to remove the script as soon as possible.
What does this mean for your webshop?
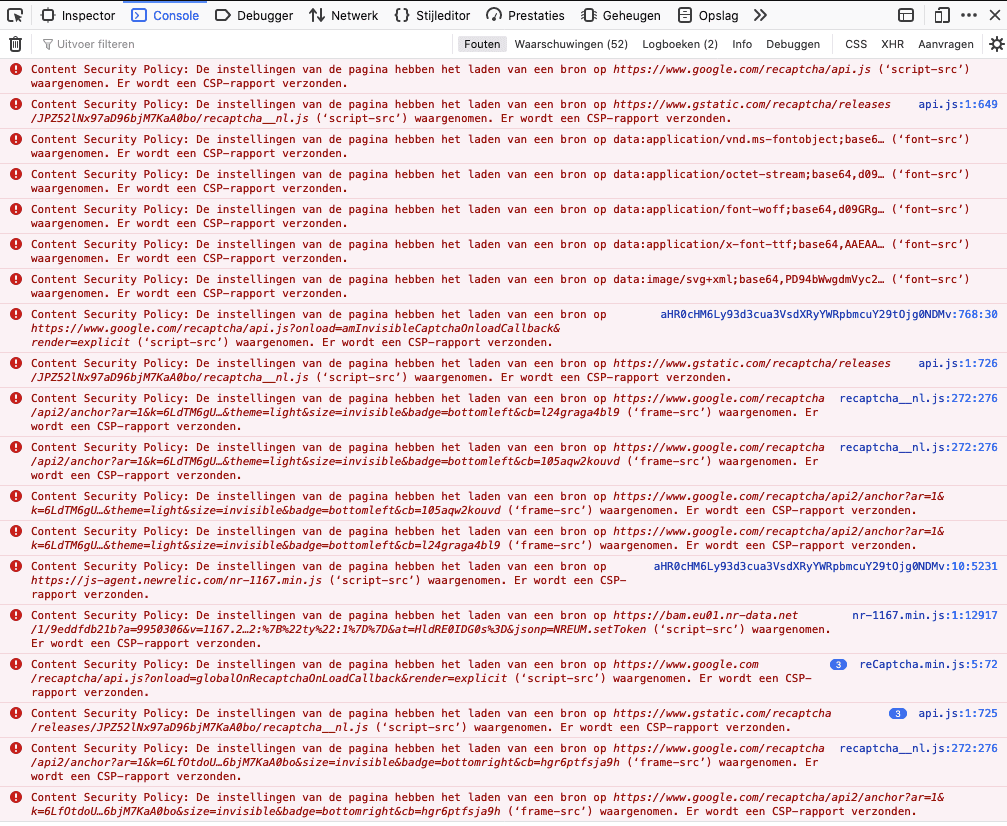
CSPs are not new and are already used on many websites. However, Magento only introduced this functionality with version 2.3.5 and turns it on by default when updating. By default, CSP is set to report-only mode, meaning it reports only the scripts that have not yet been added to the CSP. In your browser console you will see the error messages coming back, see the attachment for an example of the error messages. Nothing else is blocked yet. Logical, otherwise part of your website would no longer work when the CSP has not yet been set up (properly).
After you make up your CSP, the advice is the so-called Restrict mode enabled on your website, actually blocking scripts if they are not included in the CSP. Only then do you have more assurance that your shop remains safe in case an unauthorised script is placed. The disadvantage of this mode, however, is that scripts you add to the shop must first be added to the CSP before they work. This can be annoying, for example, when you want to apply marketing or analytics scripts such as Hotjar. Magento is expected to introduce the restrict mode will adopt as the standard in later versions. So it is wise to apply this properly now.
Because the CSP can only be adjusted directly in the code, this is something you, as a webshop administrator, cannot easily implement yourself via the configuration of Magento. This has to do with security: if a hacker has access to the webshop, he can add his own script to the CSP. Your webshop builder can help you with this by creating the CSP for you and setting the desired mode. First, the website must be scanned for scripts that are loaded on your website. Next, the scripts have to be added to the CSP, after which the site has to be monitored whether everything is still working as desired. If desired, the restrict mode are handled. Should you later want to activate a new script in the webshop, you can submit it to the website builder so that it can also be added to the CSP.
If you need help implementing the CSP, we can support you. Visit contact with us for questions, comments and the possibilities.